🔒 Payments Threat Modeling
Guarding the Digital Fortress: Unveiling the Power of Threat Modeling
Welcome to The Engineer Banker, a weekly newsletter dedicated to organizing and delivering insightful technical content on the payments domain, making it easy for you to follow and learn at your own pace.
Want free access to paid posts like this one?
Summary
Threat modeling in payment systems is crucial for identifying and addressing security threats in the rapidly evolving digital payments landscape. This article emphasizes the importance of cybersecurity, heightened by increased regulatory scrutiny and the severe consequences of data breaches. It details a structured approach to threat modeling, involving collaborative meetings where teams scrutinize their system's architecture against potential threats. Key areas of focus include authentication, authorization, data validation, and configuration management. This proactive process is vital in ensuring robust security measures, safeguarding consumer data, and maintaining trust in payment systems amidst a broad spectrum of risks.
Greetings and welcome to another installment of our security series! Threat modeling in the realm of payment systems is a crucial process that involves identifying, assessing, and addressing potential security threats. This proactive approach is vital in the constantly evolving landscape of digital payments, where new technologies and methods are perpetually introduced, bringing along their own set of vulnerabilities and risks.
In the early days of electronic payments, the primary concern was the physical security of transaction data. However, as technology advanced and digital transactions became more prevalent, the focus shifted towards cybersecurity. Today, threat modeling in payments encompasses a broad spectrum of potential risks, from data breaches and fraud to system outages and compliance violations.
The importance of threat modeling in payments is further highlighted by the increasing regulatory scrutiny in this sector. Data protection regulations like GDPR (General Data Protection Regulation) in Europe and various state-level laws in the United States impose strict penalties for data breaches. This regulatory environment makes it imperative for payment providers to adopt robust security measures to protect consumer data.
Moreover, the reputational damage from security incidents can be severe. Consumers trust payment providers with their sensitive financial information, and a breach of that trust can lead to loss of business and long-term damage to a company's reputation. In our comprehensive article linked below, we delve into essential security properties that are imperative to validate as you approach the launch of your product. You can utilize this article as a foundational reference for the current one.
Also, explore our comprehensive article on SIEM, learn how Security Information and Event Management systems empower proactive threat detection and response, forming a vital part of a robust cybersecurity strategy:
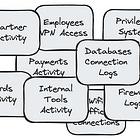
Threat modeling consists of a series of structured meetings where teams systematically analyze and contrast their system's architecture and design against potential security threats. This process is not merely a one-off exercise but an ongoing practice integral to the lifecycle of a system, especially in high-stakes environments like payment processing. During these meetings, participants from various disciplines – including software development, network engineering, security, and often representatives from compliance and risk management – collaborate to scrutinize every aspect of the system's architecture. The objective is to ensure that the system is not only robust in its current state but also prepared to withstand evolving security threats and challenges. Engaging in these discussions will provide you with a critical perspective, allowing you to examine and evaluate your product exclusively through the lens of security.
Below, you'll find a possible guide to structure your threat modeling meetings and the topics to be addressed within each. Often, teams are unable to complete the entire threat modeling process in a single session, so additional sessions may need to be scheduled.